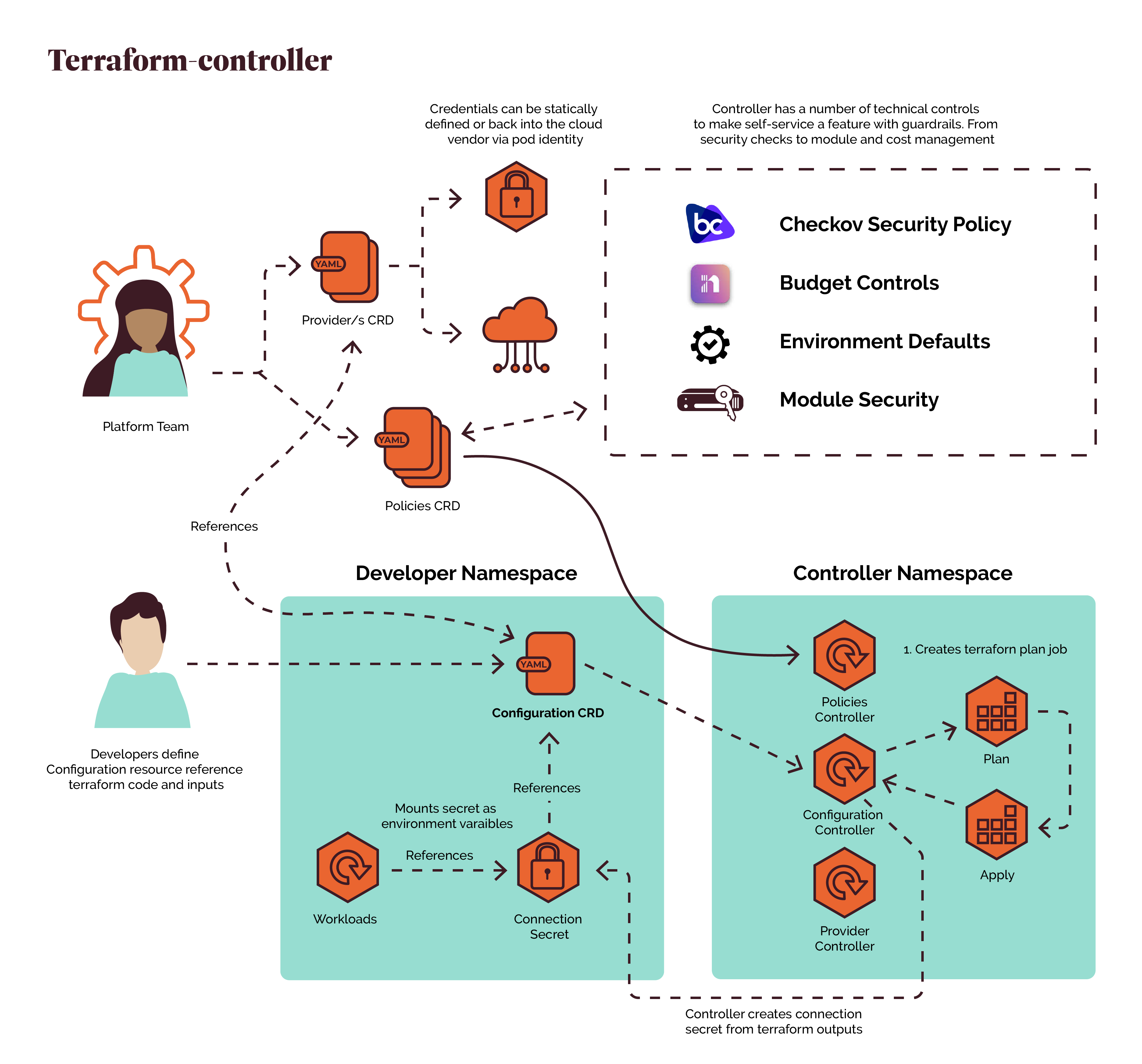
为防止恶意用户进行暴力密码破解,需要对ssh远程连接进行登录限制,需修改密码复杂度、密码有效期、失败登录次数、登录超时及失败登录用户锁定。
ssh远程登录限制
检查pam_tally2模块
[root@rac1 ~]# whereis pam_tally2
pam_tally2: /usr/sbin/pam_tally2 /usr/share/man/man8/pam_tally2.8.gz修改配置文件
限制服务器tty终端
编辑/etc/pam.d/system-auth或/etc/pam.d/login文件均可(因为login使用了system-auth)。在文件中增加:
auth requisite pam_tally2.so onerr=fail deny=3 unlock_time=60 even_deny_root root_unlock_time=60
account required pam_tally2.so限制SSH远程登录
检查sshd配置是否开启PAM
[root@rac1 ~]# grep '^UsePAM' /etc/ssh/sshd_config
UsePAM yes普通帐户和root的帐户登录连续3次失败,就锁定1分钟。
如果不想限制root帐户,可以把even_deny_root及root_unlock_time参数去除。
root_unlock_time:表示root帐户的锁定时间(秒)
onerr=fail:表示连续失败
deny=3:表示超过3次登录失败即锁定。
编辑/etc/pam.d/sshd文件在其中添加如下内容:
auth requisite pam_tally2.so onerr=fail deny=3 unlock_time=60 even_deny_root root_unlock_time=60
account required pam_tally2.so如不存在/etc/pam.d/sshd文件则新建文件,并填入如下内容:
[root@localhost ~]# vi /etc/pam.d/sshd
#%PAM-1.0
auth required pam_sepermit.so
auth substack password-auth
auth requisite pam_tally2.so onerr=fail deny=3 unlock_time=60 even_deny_root root_unlock_time=60
auth include postlogin
# Used with polkit to reauthorize users in remote sessions
-auth optional pam_reauthorize.so prepare
account required pam_tally2.so
account required pam_nologin.so
account include password-auth
password include password-auth
# pam_selinux.so close should be the first session rule
session required pam_selinux.so close
session required pam_loginuid.so
# pam_selinux.so open should only be followed by sessions to be executed in the user context
session required pam_selinux.so open env_params
session required pam_namespace.so
session optional pam_keyinit.so force revoke
session include password-auth
session include postlogin
# Used with polkit to reauthorize users in remote sessions
-session optional pam_reauthorize.so preparepam_tally2命令
查看失败次数
[root@rac1 ~]# pam_tally2 --user root --reset
Login Failures Latest failure From
root重置失败计数
[root@rac1 ~]# pam_tally2 --user root
Login Failures Latest failure From
root 0 登录超时时间限制
[root@rac1 ~]# vi /etc/profile
TMOUT=600
[root@rac1 ~]# source /etc/profile密码过期设置
- PASS_MAX_DAYS:新建用户的密码最长使用天数
- PASS_MIN_DAYS:新建用户的密码最短使用天数
- PASS_WARN_AGE:新建用户的密码到期提前提醒天数
查看当前密码过期设置
[root@rac1 ~]# egrep '^PASS_MAX_DAYS|^PASS_MIN_DAYS|^PASS_WARN_AGE' /etc/login.defs
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_WARN_AGE 7用户密码强度设置
编辑/etc/pam.d/system-auth文件在其中添加如下内容:
至少8位,包含一位大写字母,一位小写字母和一位数字
password requisite pam_cracklib.so minlen=8 ucredit=-1 lcredit=-1 dcredit=-1 ocredit=-1示范:
[root@rac1 ~]# vi /etc/pam.d/system-auth
#%PAM-1.0
# This file is auto-generated.
# User changes will be destroyed the next time authconfig is run.
auth required pam_env.so
auth required pam_faildelay.so delay=2000000
auth sufficient pam_unix.so nullok try_first_pass
auth requisite pam_succeed_if.so uid >= 1000 quiet_success
auth required pam_deny.so
account required pam_unix.so
account sufficient pam_localuser.so
account sufficient pam_succeed_if.so uid 参考文档:
https://blog.csdn.net/sumengnan/article/details/114144601
https://blog.csdn.net/weixin_46505978/article/details/120348264
https://www.cnblogs.com/zhengna/p/13154168.html
文章来源于互联网:centos7配置身份鉴别安全功能